Windows/WSL hardware ssh & gpg keys
Continuing with the topic of ssh keys on Linux in a TPM, what options are available for Windows+WSL?
WSL access to the TPM
As far as I can tell, using a TPM in WSL is not an option. There's a tool to send raw data to the tpm, but it doesn't seem to have enough functionality to handle gpg/ssh keys.
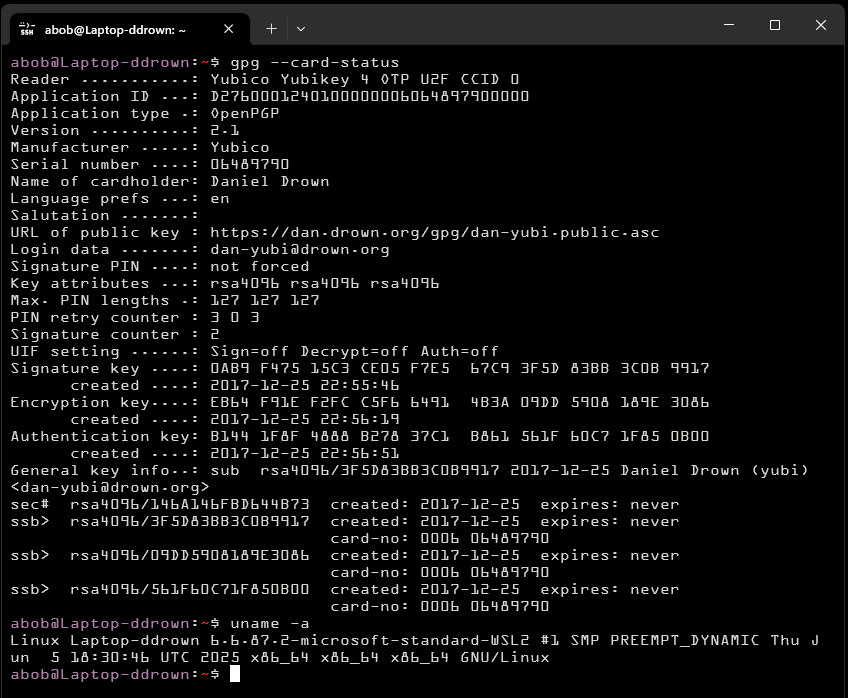
GPG Hardware Keys
For gpg keys, the only option I've found is yubikeys. This involves installing windows gpg and running gpg-agent.exe. To use the keys from wsl, you'll need to forward the gpg-agent unix socket to gpg-agent.exe's tcp socket.
I've created a go program to do that. The repo has systemd user config files to take over $XDG_RUNTIME_DIR/gnupg/S.gpg-agent. Once that's done, wsl gpg will have access to the yubikey.
SSH Hardware Keys
I've already gone over setting up U2F/WebAuthn ssh keys in windows, which provide a hardware-protected key. Additionally, you can generate a key using the Windows Hello based WebAuthn, which ties into Window's fingerprint/pin authentication.
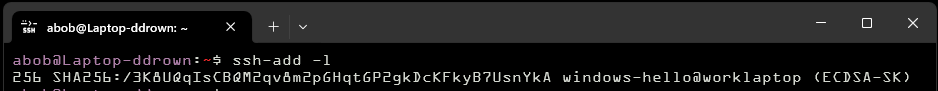
Because you can only run one ssh-agent.exe in Windows, I'm using ssh-agent-filter to make only some keys available when agent forwarding. I'm giving the filtered ssh agent socket to the ForwardAgent config. If this were the openssh ssh-agent, I could use agent forwarding restrictions instead.
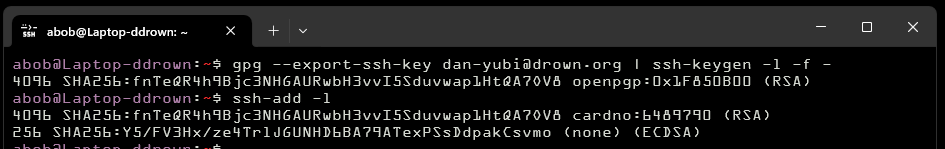
You can also use my gpgagentrelay program to forward to the gpg-agent's ssh socket from $XDG_RUNTIME_DIR/gnupg/S.gpg-agent.ssh, but I could only get this to work if I put the keygrip into %AppData%\gnupg\sshcontrol. Agent forwarding in ssh doesn't seem to work with gpg-agent.exe, gpg-agent complains about the agent forwarding restrictions.
Questions? Comments? Contact information
